Customized Risk Profiles with Merge.io
Converting mounds of vulnerability scan data into operational action is a challenge that many organizations have. One major part of that challenge is how to go about systematically boiling down the volumes of vulnerability data to get to the vulnerabilities that you need to fix.
This is especially crucial when dealing with internal scans of larger networks. Internal vulnerability scanning tends to be a tricky process due to the fact that in most cases there is very little access control that is implemented between the scan engine and the target systems. With little access control in place, the vulnerability scanners produce a lot of vulnerability data to analyze. The question still remains – how do you make the most sense of the volumes of data that is generated?
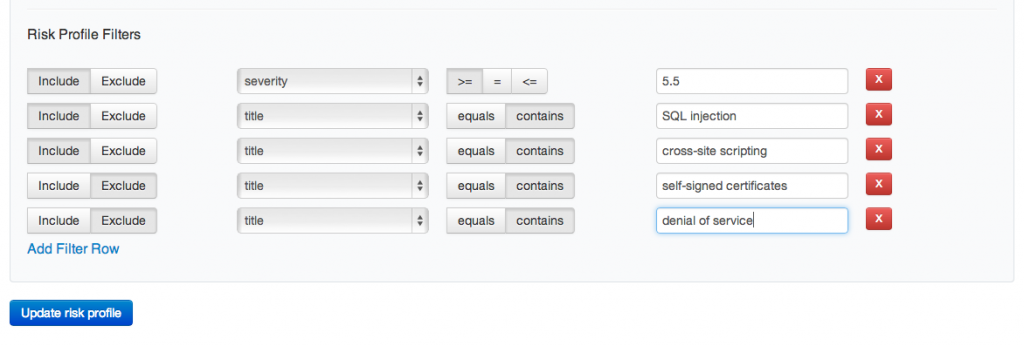
We begin with a policy and a process. Does you have established remediation thresholds for ranked vulnerabilities and has management signed off on it? If not, start your journey here. Build an organizational policy that establishes a base set of conditions that determine which vulnerabilities must be remediated vs. vulnerabilities that are acceptable in a given environment. As an example policy/process may state that you remediate (per the defined remediation thresholds) any vulnerability that meet the following criteria for internal scans:
- CVSS score of 5.5 or greater
- SQL injection
- Cross site scripting
Since these are internal scans, there will be certain vulnerabilities that we will choose not to remediate. This could be due to environmental variables, compensating controls, etc. Examples of these may include:
- Self signed certificates
- Denial of service vulnerabilities
These are obviously just examples, but each organization generally has vulnerabilities they want to remediate and vulnerabilities that they don’t due to acceptable levels of risk. So how do you apply this logic in an automated fashion to our vulnerability data? The reality is that most companies that I deal with are still using Excel (the duct tape and bailing wire of the business world) to accomplish this. And even with the use of spreadsheets, the process is highly manual.
This is where Merge.io can help out. With Merge.io you can create custom risk profiles that can determine which vulnerabilities from the imported data sets to remediate and which to exclude for acceptance. Just create the profile using the risk profile builder and apply it to a scan import. All of the vulnerabilities that match your include criteria will be added to the Merge.io workflow system. And the vulnerabilities that match the exclude filter will be excluded from workflow tracking.
Risk profile filters can be built that examine vulnerability CVSS score, Risk rating, title description, port, service, operating system and more.
These filters are available for use with any scan imported into Merge.io. They can be built to match your internal remediation standards and they can be added to over time as the organization changes. This provides an automated, repeatable approach to managing the volume of data that vulnerability scans can create.
Merge.io has a built-in filter for PCI that matches the requirements laid out by the PCI ASV Program Guide Version 2.0. Additional compliance filters are coming soon!
Be sure to check out Automated Scan Validations with Merge.io.
Sign up for a free 60 trial account on Merge.io!